Can You Power a Phone With a Capacitor? And, can we understand that?
Posted on | June 9, 2013 | No Comments
“There was a recent news item regarding a teenager’s project to use a super capacitor as a quick-charging energy storage device. The primary claim is that this could be used to fully charge a phone in just 30 seconds.”
http://www.nbcnews.com/technology/teens-invention-could-charge-your-phone-20-seconds-1C9977955
Luckily, Wired put a physicist on the case, and he discusses this in much length.
http://www.wired.com/wiredscience/2013/05/can-you-power-a-phone-with-a-capacitor/
Maybe a bit too complicated for most people.
Here s a simplified version (not precise, just testing whether this is realistic at all):
To charge a mobile phone (battery is typically 1500 mAh at 3.7 V or 5-6 Wh) in 30 secs,
you d need about 600 -700 W for those 30 seconds. Pretty hot.
The energy needed would be about 20,000 J
The energy stored in a capacitor is
W = 0.5 * C * V**2
so that wouldgive
C = 1600 F
Do such capacitors exist?
Yes, they are called supercaps, and no, Khare did not develop them.
They have been used in lost of electronics for decades.
They are inside some of the stuff you use.
You can get them on ebay:
http://www.ebay.com/itm/3000F-2-7V-Supercap-3000-Farad-Super-Ultra-Capacitor-/150642133382
A supercap of 1600 F would be a bit too big for your phone, but
since her work,
https://www.usc.edu/CSSF/History/2013/Projects/S0912.pdf
in fact looks at improving (rather than “inventing”) supercaps,
it s not entirely impossible that you d see something like this, at some point in time.
just not next week.
Her report claims
“an energy density of 20.1 Wh/kg, comparable to batteries,
while maintaining a high power density of 20540 W/kg.”
The energy density limit would make her current supercap about 250 grams –
a bit heavy still, but the right way to go and the rest, that’s gradual improvement.
So, not possible – not all bad, just reported by most media in a wrong way.
TV White Spaces Africa Forum 2013
Posted on | June 7, 2013 | No Comments
Last week i attended the TV White Spaces Africa Forum 2013
https://sites.google.com/site/tvwsafrica2013/home,
together with colleagues from the NSRC http://nsrc.org and ICTP http://wireless.ictp.it (thanks!).
It was an event organised and largely sponsored by Google in partnership with a number of other organisations,
including Microsoft http://www.microsoft.com/,
Internet Society Senegal http://www.isoc.sn/,
Afrinic http://www.afrinic.net/, APC http://www.apc.org/,
and the Senegalese Ministry of Communication, Telecommunications and the Digital Economy
https://www.facebook.com/pages/Ministere-De-La-Communication-Et-Des-Telecommunications-senegal/129113073808015.
There s plenty of tweets, https://twitter.com/search?q=%23TVWSAfrica,
and Steve Song, now also a fellow NSRCrian, has an excellent summary here:http://manypossibilities.net/2013/06/tv-white-spaces-in-africa/
– to which i’d like to add a few thoughts:
( Steve’s lines in italics, comments in bold.)
Both [Microsoft and Google] stand to benefit from having more Africans affordably online and in this particular case, their corporate goals are fairly well-aligned with a development goal.
In some areas, goals are well-aligned, in other areas – like local ownership, network neutrality, control and openness of data they are in conflict.
There is the very fundamental question of why african networks and services should be run, and user profiles and profits be harvested by non-african companies.
What stuck in my mind from this session was an interesting analogy
shared by Kai Wulff who pointed out that in Africa, taxi drivers
generally don’t fill up their tank completely but just enough to get
where they need to go. Similarly, pay-as-you-go airtime has allows for
dynamic management of phone charges. This is common knowledge but it
was a nice insight that this conceptual framework might be applied to
spectrum management.
It could be argued that the underlying logic and reasons for this,
e.g. the non-availability of capital on personal and organizational level,
should be challenged rather than solidified and capitalized on –
but that is a general comment, outside the scope of this conferences’ theme.
Arno Hart, TENET’s project manager for the [Cape Town] trial, presented the work of
the trial so far. So far 10 schools have been connected representing
more than 6400 students. So far the technology has met its most
important goal which is demonstrating non-interference with television
broadcasts,
Cape Town has more active terrestrial television broadcast
channels than most place in South Africa so it was ideal for a trial of
TVWS. The throughput and latency of the connectivity is not quite the
10mbps over 8km that has been advertised but it was still respectable
It is evident that TVWS technology is still evolving and performance
improvements can be expected.
The focus of this trial was in fact to look at interference, in an urban privileged environment, rather than at performance in a rural, low density environment, in which we see the greatest potential of this technology.
The performance as such is far from what can be achieved in the 2.4 and 5 Ghz bands, for such a link.
It lead some people to note that, performance wise, of all these trials could have been done better in spectrum that already is open (2.4 and 5 GHz)).
(… The Kenya Mawingu project: …)
A video is at https://vimeo.com/60073409 –
i d be interested in people’s comments on its narrative.
There was some discussion among the participants as to whether an
authentication database was the best approach to TVWS for Africa. Some
people argued that this was importing unnecessary limitations from the
US,
from highly developed (urban) areas rather than remote low density environments
(in which TVWS has its greatest innovative potential)
and essentially tying Africa to a western agenda and blocking innovation rather than enabling it.
It is an interesting question. On the one hand, I would like to
see TVWS achieve the same kind of success that WiFi has through an
unlicensed environment. I fear that constraints such as an
authentication database might limit the uptake of the technology.
Indeed.
Certainly, the idea of having to connect
to a remote database in order to just start equipment
is somewhat of a horror scenario for network deployers out in remote fields and community networkers alike.
But, from a regulators perspective, there is no necessity to limit equipment and innovative use in this way,
and one might hope the inextricability will not be interpreted in this way.
From an african regulators perspective, the US – or generally external – database is not needed in order to get started – databases may be build along the way, and be controlled on national or regional level.
As these databases could and will become increasingly dynamic,
they carry enormous economic value and control potential.
They add one more layer to (already impressive) corporate mapping, surveillance and profiling technology.
The question of whether they will be run and owned by private global companies
and/or national/regional organizations deserves attention.
In order for TVWS [to] achieve the same kind of success that WiFi has through an
unlicensed environment, it will take the same essentials:
unlicensed spectrum, open standards, community interest, sub-$100 gear.
Unlicensed spectrum (Wifi) – not the mobile operators spectrum – today carries the larger part of all mobile data traffic. There is something to learn from this, also for #TVWSAfrica.
the green window plug
Posted on | May 4, 2013 | No Comments
putting the green window plug into perspective:
http://grist.org/list/just-stick-this-portable-outlet-to-your-window-to-start-using-solar-power/
http://www.yankodesign.com/2013/04/26/plug-it-on-the-window/
Touche Arduino
Posted on | August 14, 2012 | No Comments
Steve Houben, Sebastian Buettrich
Arduino Touché @pITlab –
all credits & thanks: DZL, Mads Hobye
http://www.instructables.com/id/Touche-for-Arduino-Advanced-touch-sensing/
we followed their instructable 100% and it worked straight away.
Consider wireless security with EAP/802.1x completely broken / obsolete
Posted on | August 8, 2012 | No Comments
Second comment to the security debate, e.g. here
http://revolutionwifi.blogspot.dk/2012/07/is-wpa2-security-broken-due-to-defcon.html
So MSCHAPv2 is completely broken. No problem.
For EAP/802.1x wireless security, that should not matter, as we only use it inside a tunnel (TTLS, PEAP) (SSL protected).
Popular EAP/802.1x-methods: PEAP+MSCHAPv2 or TTLS+PAP or TTLS+MSCHAPv2
BUT
In most networks, on most clients, certificate validation is largely absent
and difficult to enforce across all clients (BYOD!).
Moreover, many user guidelines explicitly ask clients to NOT validate the certificate.
A very simple, realistic attack scenario:
Place a rogue AP with the right SSID and connected to a fake RADIUS server in the target building/area,
and harvest logons at leisure.
No client has any chance to even notice the attack.
So, the tunnel is broken.
The fact that MSCHAPv2 is broken – it does not even really matter:
the attacker lures the client into talking to their rogue RADIUS server,
and of course can read all user credentials, regardless of encryption.
This is NOT a little irrelevant side note to the discussion of MSCHAPv2, which is, i agree, more intellectually interesting.
The MSCHAPv2 discussion unfortunately is an interesting academic but irrelevant side note to the fact that our de-facto wireless security practices render EAP/802.1x broken.
Summary:
Unless the certificate validation problem is addressed,
we should consider current wireless security with EAP/802.1x completely broken / obsolete.
Agreed – it would not have to be, but it is.
MS-CHAPv2, widely used in WPA2 Enterprise, broken (more so than we thought)?
Posted on | August 1, 2012 | No Comments
Quoting this DEFCON 20 article
https://www.cloudcracker.com/blog/2012/07/29/cracking-ms-chap-v2/
“MS-CHAPv2 is used quite heavily in WPA2 Enterprise environments.
In their 1999 analysis of the protocol,
Bruce Schneier and Mudge conclude “Microsoft has improved PPTP to correct the major security weaknesses described in [SM98].
However, the fundamental weakness of the authentication and encryption protocol is that it is only as secure as the password chosen by the user.”
http://www.schneier.com/paper-pptpv2.html
“This, along with other writings, has led both service providers and users to conclude that they can use MS-CHAPv2 in the form of PPTP VPNs and mutually authenticating WPA2 Enterprise servers safely, if they choose good passphrases.”
Is there anything new in the attack reported here, then?
The attack focusses not on a library or guessing attack on the password but, instead on
recovering the MD4 hash of the user’s password.
A detailed look into the problem shows that what looks like a 2**128 crack job is really just a 2**56 – due to redundancies, shared bases and zero padding.
In other words, a single round DES crack.
The actual crack work is performed by a dedicated piece of hardware, “an FPGA box that implemented DES as a real pipeline, with one DES operation for each clock cycle.
With 40 cores at 450mhz, that’s 18 billion keys/second. With 48 FPGAs, the Pico Computing DES cracking box gives us a worst case of ~23 hours for cracking a DES key, and an average case of about half a day.”
This cracking engine is made accessible via “the cloud” (no comment on the cloud meme here) – an API and helper tool, free for download.
The article concludes:
“Enterprises who are depending on the mutual authentication properties of MS-CHAPv2 for connection to their WPA2 Radius servers should immediately start migrating to something else. ”
On Schneier’ blog, a comment has been requested:
“@Bruce –
Can we get a comment / response to the work presented at Defcon on MS-CHAPv2 only being as secure as a single round of DES?”
But, for something that sounds like it s going to bring down most of this planets enterprise wireless, it doesnt seem to make an awful lot of waves. Why not?
As far as wireless security (and only that!) is concerned,
does this discovery mean we need to stop using MSCHAPv2 or maybe even
EAP-TLS/PEAP/802.1x altogether, and “use something else” – as the article
somewhat vaguely says?
No.
Simplified, it doesnt matter much to Enterprise WiFi if MSCHAPv2 is broken, as we are
only using it inside protected tunnels.
Andrew von Nagy explains this much better than i could:
http://revolutionwifi.blogspot.dk/2012/07/is-wpa2-security-broken-due-to-defcon.html
I quote:
“What is the Impact to Wi-Fi Network Security?
Specifically, does this make much of an impact for Wi-Fi networks where
802.1X authentication is employed where MS-CHAPv2 is used (namely
EAP-PEAPv0 and EAP-TTLS)?
Answer – No, it really does NOT. The impact is essentially zero.”
Much more of a problem in real life wireless is the fact that on the networks i have seen, almost nobody enforces strict certificate validation.
Also, keep in mind that certificates are bound to hosts/domains/organizations, but in no way to SSIDs (whether ESSID or BSSID) or APs.
Thus, a realistic attack scenario is quite simple:
i will deploy a rogue AP and Radius server that supplies some (!) certificate (which will
never be checked for validity!), and own the EAP-TLS tunnel and hence all communication inside it, harvesting usernames and passwords as people connect.
Now THAT is a problem.
The fact that i speak open inside the tunnel is not a problem, really,
as long as we know who owns the tunnel.
So, we can more or less ignore the MSCHAPv2 hack and focus on certificates instead.
ps. Thanks NSRC colleagues for heads up and thanks to my colleague Felix here at ITU, for discussion!
Raspberry Pi – first boot
Posted on | June 8, 2012 | No Comments
1. Physical connections
DVI screen, network, usb keyboard, power.
2. Prepare SD card
I m using Debian Squeeze as supplied here: http://downloads.raspberrypi.org/download.php?file=/images/debian/6/debian6-19-04-2012/debian6-19-04-2012.zip
It s the “image we recommend you use. It’s a reference root filesystem from Gray and Dom, containing LXDE, Midori, development tools and example source code for multimedia functions.”
Downloaded it, insert SD card, which in my case mounts as /dev/sdb1
# umount /dev/sdb1
# dd bs=1M if=~/Downloads/debian6-19-04-2012/debian6-19-04-2012.img of=/dev/sdb
1859+1 records in
1859+1 records out
1950000000 bytes (2,0 GB) copied, 947,865 s, 2,1 MB/s
3. First boot
Inserting it into the Pi.
Not so good: the card sticks out from the board quite a bit.
Well. nobody said to expect a cased designer product.
Power supply is known to be critical – i ve chosen a 5V/1200 mA – that should be margin enough.
Plug it in, boots without a problem.
Log in – some people noticed that the Pi comes with english keyboard settings as standard, so check whether you are QWERTY or QWERTZ.
Run
# dpkg-reconfigure locales
as root to adjust your locales settings.
4. Summary so far
No surprises, install and boot is easy, following the guides linked from the raspberry site –
and some guides out there .
http://www.heise.de/hardware-hacks/artikel/Erste-Schritte-mit-dem-Raspberry-Pi-1573973.html (german)
Now we are starting running various tests, trying different images, seeing how the CPU copes, whether the board gets hot, etc.
to be continued
Solar power on 11 pages
Posted on | May 10, 2012 | No Comments
Here is a little introduction to photovoltaics, written in the context of a project at a school in Nepal,  and primarily meant for school students from 12 – 20 years, with varying degrees of maths and science skills.
and primarily meant for school students from 12 – 20 years, with varying degrees of maths and science skills.
So, it s an attempt to explaining the basics of photovoltaics in a simple way.
Your comments, corrections and critical remarks are most welcome!
In case you would like to help improve it, let me hear from you.
X-CTU on Linux Ubuntu 10.04
Posted on | February 3, 2012 | No Comments
Using Digi XCTU on linux (ubuntu 10.04)
Digi XCTU,
http://ftp1.digi.com/support/documentation/90001003_A.pdf (last verified: Feb 2012)
is a utility for configuring xbee modems.
While it is a Windows application, it can easily be made to work on Linux.
The following is no new information,
rather just a confirmation and
documentation of making this work on Linux Ubuntu 10.04
Before we start, some tips for XCTU in general, not specific for Linux:
- Be patient! Be really patient! XCTU communication can be really slow, and often it will fail. When that happens, take your time, and systematically try all different connection settings. For example, you may think that your modem is at 38400 baud, but for some reason, it doesnt remember that – and will answer OK on 9600 baud anyway.
- Always save and archive configurations, and save them with good names that will let you know which is which – it will save you a lot of time.
Now, the Linux part:
(the following steps to be performed as root or via sudo)
0) Install wine
apt-get install wine
and configure it, using the Configure Wine menu item in your Applications menu.
You dont need to make any changes. It will create the .wine directory under your user directory.
1) Prepare symlinks
in ($HOME)/.wine/dosdevices, do
ln -s /dev/ttyUSB0 com5
ln -s /dev/ttyUSB1 com6
ln -s /dev/ttyUSB2 com7
ln -s /dev/ttyUSB3 com8
This is the main step really – it maps Linux’s serial ports (called tty) to Windows’ COM ports.
2) Download XCTU
http://ftp1.digi.com/support/utilities/40003002_B.exe
(at the time of writing – this might change.)
chmod this file to be executable:
chmod 755 <filename>
3) Open XCTU installer with wine program loader
Right click the file in folder view, open with Wine program loader,
follow install dialogue, no surprises or probs there.
4) Insert USB gateway with xbee module on it
Check which port it connects to by doing
ls -ltr /dev/tty*
or
grep USB /var/log/syslog
5) Start x-ctu via wine menu.
It should open without probs.
6) What will not work
Automatic firmware updates via web do not seem to work – you will have to get firmware updates manually, from
http://www.digi.com/support/productdetail?pid=3661 (at the time of writing, 20 feb 2012) and put the zip files in the xctu updates directory, e.g.
<yourhome>/.wine/drive_c/Program Files/Digi/XCTU/update
Then add them via the XCTU menu item
“Downlaod new versions” >> “from file”
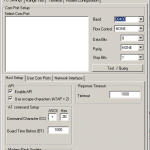
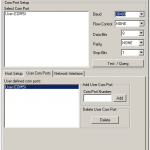
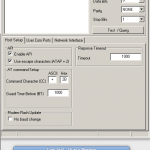
7) Examples, screenshots
then follow the typical xbee modem configuration process, as described elsewhere, e.g. in pdf linked above or Rob Faludis book,
http://shop.oreilly.com/product/9780596807740.do
In order to communicate, XBee modules must use:
Here s some examples of my settings with some screenshots.
set BAUDRATE 38400
use API
PC settings, user com port – add our port here:
TEST QUERY MODEM answers OK
Modem Configuration – Read
Set Function Set ZIGBEE ROUTER API
Set PAN ID = 666
Channel = yr choice
SERIAL INTERFACING
Baud rate 38400 = 5
API = 2
Addressing
DH and DL both = 0
How to boot from USB in virtualbox on Ubuntu
Posted on | May 13, 2011 | No Comments
Useful for quick testing of USB boot media, flexible plug’n’play of guest operating systems, and so on.
Tested for various Ubuntu 9/10, virtualbox 3.1.6/4.0.6
Prepare:
$ su # mkdir /root/.VirtualBox/HardDisks # VBoxManage internalcommands createrawvmdk -filename \
/root/.VirtualBox/HardDisks/usbdisk.vmdk \
-rawdisk /dev/sdb1
Note: all in one line! the last bit, the device name, needs to point at your USB drive. In this case /dev/sdb1 – yours will be different!
So, you tell virtualbox to see the USB drive as a disk, which you then boot from.
Open virtualbox:
# virtualbox
Make new machine, choose “Existing harddisk” and point at the one you created.
Thats all.
Thanks, Three Wise Men http://www.twm-kd.com/software/boot-virtualbox-machine-from-a-usb-flash-drive/
« go back — keep looking »